Vulnerable Software: Maharashtra State Electricity Board (MSEB) iOS Application
Vulnerability:Sensitive Information Exposure via GET Method
Affected Version: Up to 16.1
Fixed Version: No Fix Available
Vendor Homepage: Link
CVE: CVE-2021-41719
CVE Author: Tejas Nitin Pingulkar
Exploit Available: POC
About Affected Software
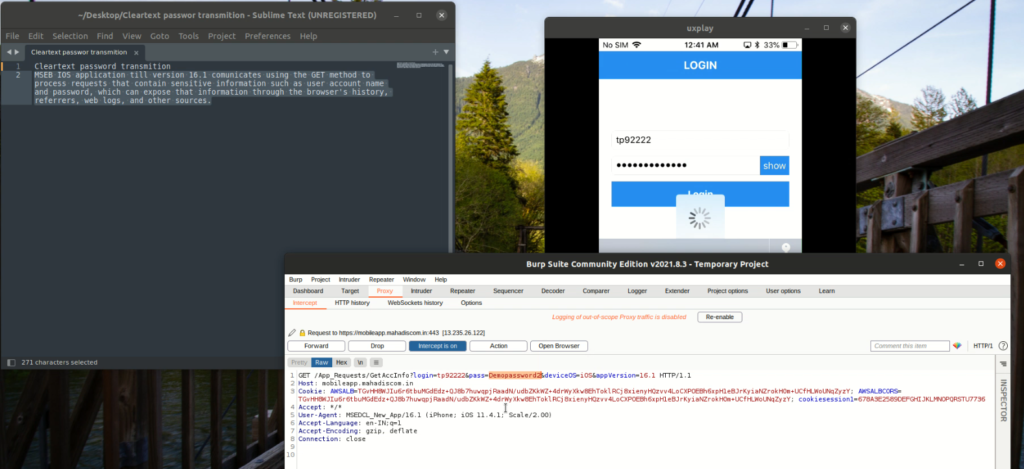
The MSEB iOS application (up to version 16.1) improperly uses the GET method for processing requests containing sensitive user credentials, including account names and passwords. This exposes user authentication details to several risks:
- Stored in Browser History – Any user or malware accessing the device can retrieve login credentials from history records.
- Logged in Web Server Logs – Web access logs may store sensitive data, making them retrievable by attackers.
- Exposed via Referrer Headers – If a user navigates to another site, their credentials may be leaked in the HTTP referer field.
- Interceptable by Network Attacks – Traffic monitoring or proxy interception (e.g., via Wireshark, Burp Suite) can reveal sensitive details.
.
Exploit
1. Intercepting the Request
- Install Burp Suite to monitor network traffic.
- Open the MSEB iOS app and attempt to log in.
- Observe the GET request containing password
- The URL parameters expose login credentials in plaintext.
POC: